Sorry, most articles are not available in English yet
The Programs
Burn or rip a DVD
The first thing you need is having ad DVD-drive besides the drive in which your CD from IT-Politisk Forening placed in. Otherways you cannot use our CD in a live-CD. Well, you could also copy that CD onto a hard disk drive, but that is another story.
Normaly video-DVDs have a size upto 9 GB, but most DVD-burning drives vill only accept up to about 4,7 GB. The normal solution is compressing the DVD. Another solution is copying the DVD to a hard disk and then burning two TVDs, but we will explain the first solution.
Put the video DVD into your DVD-drive. A box will pop up, but you will just close that box. Instead you will go to the K-menu > multimedia > "DVD backup software (k9copy)". The program K9copy will proabably allready have found your DVD-drive as input. I K9copy you will choose File > Open. Now the program will examine the DVD. In the tab "DVD" a DVDVOLUME will show up with the titles from the DVD. You might select just some of the titles. If you want the complete DVD, then checkmark DVDVOLUME. Now you have two options:
1. You can selct a ISO-Image as output in k9copy
Select the tab "Settings". Her you will write the location on the hard disk for your DVD-image. There must be room for 10 GB. After that you go to the action menu and select "copy".
After a while you will be asked where to save a ISO-file. You do just that and a short time after you will se a folder (dvd) and a ISO-file. Basically they contains the same and they both have the same size about 4,5 GB. You can use the folder, if you want to store the DVD on a harddisk.
You use the ISO-file in order to burn a DVD. That can be done by loading a blank DVD in the DVD-drive, and from the K-menu > multimedia > CD & DVD burning (k3b). In the program k3b you have two file- and folder fields. Use these to navigate to your ISO-file. After clicking the ISO-file a box will open. Check if the information her appears reasonable and click start. After quite a while you have a video-DVD that is useable in a video player.
2. Select your DVD-drive as output in k9copy
Now select the tab "Settings". Here you will check mark "auto burn". There must be room for 5 GB. Go to the Action menu and select "copy". A little later k9copy will complain that it cannont burn the DVD placed in the drive - and no mysteri in that! You exchange it with a blank DVD and ask the program to continue. After a while you DVD is finished.
Compressing naturally gives some detoriation in quality. You will hardly notice it using your copy in an ordinary DVD-player and watching it on TV. If you want to keep the original quality, you can rip your DVD the following way:
Make a compressed file on your hard disk.
After loading your DVD in the drive a box will pop up. You select the option to open the DVD in a new window. Now you will see two folders: audio_ts and video_ts. Now you can copy these two folders at an appropriate place on your hard disk. If your wish is to obtain a hi quality and compressed version, you will write the following in a command window:
mencoder dvd://0-8 -ovc xvid -xvidencopts pass=1 -alang en -oac copy -o /dev/null
mencoder dvd://0-8 -ovc xvid -xvidencopts pass=2 -alang en -oac mp3lame -lameopts vbr=3 -o DVD-VIDEO.avi
"DVD-VIDEO.avi" should be replaced with the path to the place on your hard disk, where you want to store your avi-file. "dvd://0-9" takes it for granted that, there exist 9 vob-files in your folder "video_ts" numbered 0 to 8. If your number af files is different, you must adjust accordingly.
Virtual Machines
Virtual machines and emulators are programs that acts like a whole computer. This way, you can run an entire operating system inside a window - and the operating system will just think that it is running un its own, real computer. That has some practical advantages. For example, it is possible to run our Linux based "Polippix" CD on a Windows computer without leaving Windows. It is also possible to run Windows inside a single window on a Linux computer, or a Mac. Or, you can run programs for a completely diffent platform - e.g. to play old Commodore 64 games.
Emulating for Security
One good use for emulators is to enhance privacy. By running suspicious programs inside an emulator, it will be more difficult for those programs to access data on your hard drive (unless you allow them access).
Virtual Machines
- Qemu is a Open Source emulator, running on Windows, Linux, Mac, Solaris. It is able to run both single programs and whole operative systems, and it can emulate several processors. Qemu for Windows is included on this CDand can run Polippix.
If you want to run the downloaded Polippix image from a windows command prompt, you can write:
-
qemu.exe -L . -m 260 -cdrom polippix.iso -localtime
the "-m" option tells how many MBytes Qemu is allowed to use.
- VMWare is not Open Source, but does have a freeware client that is able to run the Polippix.
Polippix in QEMU
EtherApe
What goes on at your network?
Computer networks are constructed in such a way that it is possible to eavesdrop on the traffic on the local network that you are connected to. This implies that if you are part of a wireless network or share a switch/hub with others, then you can follow their traffic.
Exactly how much you will be able to see depend on the type of network you are connected to. In some networks, you can see all traffic while other networks only let you see so-called "broadcast" traffic. But even the broadcast traffic will give you an idea about what is going on at your network.
No matter what kind of network you are connected to there is, however, at least one computer that will let you see all traffic to and from it. That is your own computer.
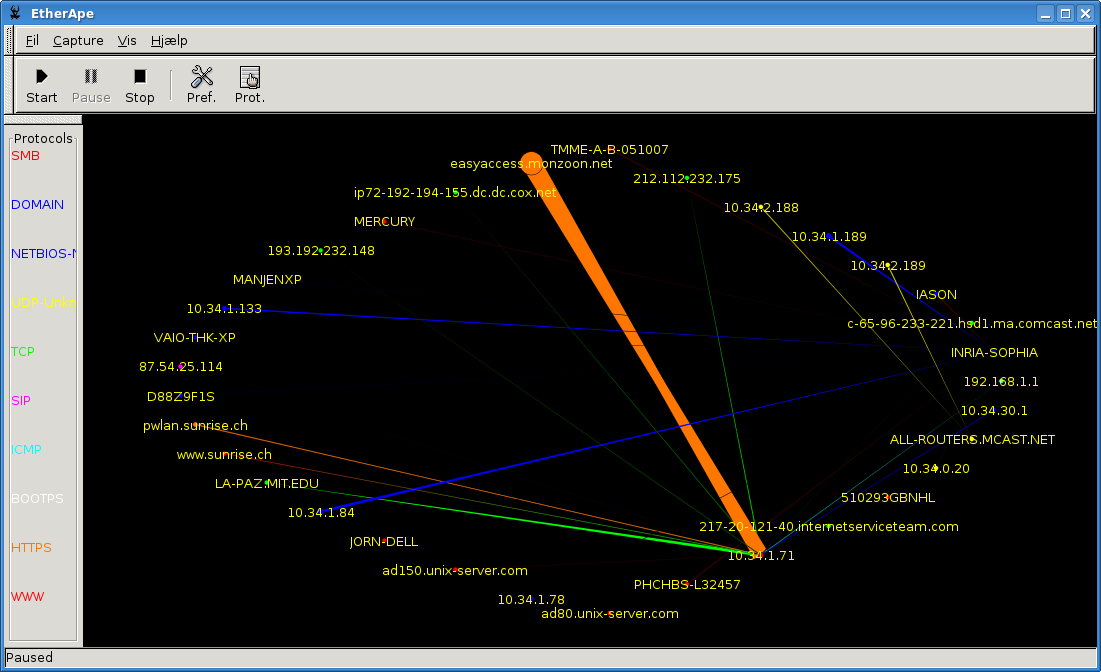
With the program EtherApe you can watch who is communicating with whom on your local network, and not the least you can get insight into who your own computer is "talking to". Just start the program and wait a while. Then you should be able to observe the traffic. Every line in the EtherApe window represents a data connection. The thicker the line, the more data is exchanged.
We have two reasons for including EtherApe on this CD:
EtherApe is an excellent tool to keep an eye what your computer is doing. Observe if it is contacting somebody that you did not expect.
We want to demonstrate how easy it is to spy on a network. You will only see fragments of who are talking to whom. But your internet provider also has a local network: All the traffic of their customers goes through their network. If your provider is running a program like EtherApe, then he can see who all of his customers are talking to.
Recent European data retention laws even make it mandatory for the internet providers to observe traffic this way - and keep that information as log files. In Denmark, for example, the internet providers have log every data connection made by their customers and keep the log files for at least one year. Then the police can demand to get this information when they want it.
If you try out EtherApe on a network that has a bit of traffic you might be surprised to learn how much is revealed about everybody. However, there are several programs that can shows much, much more than EtherApe. They will show the contents of emails, homepages and much more. Even passwords can be extracted, unless you use a encrypted connection. We could have put one of those programs on this CD, but instead we opted for EtherApe, since it only reveals reasonably inoccent information ...
About This CD
The Polippix CD was made by IT-Political Association of Denmarkto demonstrate the possibilities of IT and the consequences of certain IT-related legislation. We hope that this CD will help legislators to better understand IT, and help citizens to avoid some of the negative consequences of overly restrictive and invasive legislation.
IT-Political Association of Denmark works with the subjects presented on this CD as well as many other IT-related subjects.
The Polippix CD was originally based on the Knoppix GNU/Linux distribution, but is now based on the Kubuntu GNU/Linux distribution.
All software on this CD is free, open source software. You may distribute it at no cost, and you can get the source code for all software from Kubuntu. For the specific licenses, please refer to the license for each peace of software.
All texts on this CD that are written by IT-Political Association of Denmark can be copied under the Creative Commons Attribution-Share Alike 2.5 Denmark license. If you make any deriative work that you think might benefit the users of the CD, please let us now about it.
Further Development
All source code for the changes we made to Kubuntu to get this CD, can be found on www.polippix.org. Here you can build your own version of the Political CD, or you can prepare it together with IT-Political Association of Denmark. Of course, you can also just download the CD.
Get Involved
We always aim to make this CD better, and we would appreciate any help we can get:
Make A Version In Your Language
Translate our texts into your language. Research local legislation to find examples and facts from your country. Find out whether it is legal to distribute and use this CD where you live.
Decide whether there are IT-political issues in your country that are not represented on this CD. Is there any software that might help demonstrate those issues.
Improve Texts
Some of the texts still need work. Help proof-reading, or expand on some of the descriptions.
Configure Software
We have configured the software on this CD as much as we could. But there is still a long way until everything on the CD works perfectly. Help us create the optimum configuration for demonstration purposes. For example, try to find out how we could get encryption working in an email client.
Research Software And Technologies
Is there any free, open source software out there that should be on this CD - but isn't? How can we offer more technologies for privacy or other issues? For example, how can we use steganography?
Create Artwork
We can always use illustrations, splash screens, backgrounds, web design - and a logo for the polippix.org home page.
Come along!
Visit www.polippix.orgif you want to help out, or just have ideas or suggestions.
k3b
Copying CDs og DVDs
Media now and then bring reports about pirate copying of music and movies. Teenagers are demanded to pay thousand of dollars for copying music, and the record industy (represented by IFPI, RIAA and local copyright agencies) threaten to sue citizens, if they make illegal copies.
Ordinary citizens have a hard time trying to figure out when they legally may copy a CD or a DVD. For this reason many people refrain completely from copying, while others just copy what they want. In many countries, not even legislators can give a clear answer to what may be copied and when.
Of course, the record and movie industry wants you to think that you may not copy anything at all, and have to buy several copies of the same CDorDVD. Many DVD's even falsely claim that you are not allowed to copy them at all. However, this is not decided by the DVD authors, but by the legislation in your country.
In this international version of this text, we cannot describe laws in every country in the world, so it is up to you to find out which rules apply in your country.
In most countries, though, it is perfectly legal to make a copy of your own CD or DVD for your own, personal use (e.g. as a back-up, or for having something to play in your car). But how can you copy a CD or DVD?
Burn a DVD or CD
Right now, your DVD/CD drive contains the Polippix CD. So right now, you cannot use that drive to make copies. In order to make a copy, you need at least two CD/DVD drives in your computer. (This is of course not the case if you install our CD or another Linux on your hard drive, but that is a completely different story.)
The bottom line is that if you have a free CD-ROM writing drive, it is very easy to copy a CD. Simply start the "k3b" program and choose "Copy CD".
DVD's are a bit morecomplicated: A normal video DVD contains up to 9 GB, but most DVD writing drives can only write DVD's containing up to 4.7 GB. So if you do not want to split the DVD to two discs, you will have to compress it to make it take up less space:
- Put a video DVD in your free DVD drive and start the "k9copy" program.
- Choose File -> Open. The program will then examine the DVD.
- Under the tab "DVD" you will now get a DVDVOLUME containg the titles that is found on the DVD. You can choose all of them by checking the box next to DVDVOLUME, or you can just choose the titles you want.
- Now, click on the "Settings" tab and tell where on your hard drive you want to store your temporary DVD image. You must have at least 10GB free space.
- Click on the "Action" menu and choose "copy".
- After a long while you will œbe prompted for where to save an ISO file.
- When you have done so, you wiœll have a folder (called "dvd") and an ISO file. They basically contains the same in two different formats, and they both take up approx. 4.5 GB of disk space.
- The folder can be used if you want to keep a copy of your DVD on your hard drive instead of on a DVD disc.
- The ISO file can be used to burn a DVD. To do that, put a DVD in your DVD writing drive and start the "k3b" program.
- Then, choose "Burn ISO DVD image".
- Find your ISO image made in the steps above and click "Burn" and then "Start".
- After a long while, you will have a video DVD that you can put in your DVD player.
Since your DVD has been compressed to fit on at DVD disc with lesser capacity, there will be a certain degradation of quality. However, it is so little that you probably will not notice it if you put your DVD copy in an ordinary DVD player and watch it on an ordinary television set.
If you want to preserve the original quality from the DVD, you will have to copy it this way instead of the above:
- When you put your DVD in your free DVD drive, a box will pop up. Choose to open the DVD in a new window.
- The new window will show an audio_ts folder and a video_ts folder. Copy both folders to a suitable space on your hard drive.
- Start a command window and write
mencoder dvd://0-8 -ovc xvid -xvidencopts pass=1 -alang en -oac copy -o /dev/null
mencoder dvd://0-8 -ovc xvid -xvidencopts pass=2 -alang en -oac mp3lame -lameopts vbr=3 -o MYVIDEO.avi
MYVIDEO.avi must be the place on your hard drive where you want to put your copy.dvd://0-8assumes that there are nine .VOB files in the video_ts folder, ennumerated from 0 to 8. If there is another number of files, you need to use that instead- - Delete the audio_ts and video_ts folders from your hard drive - you do not need them anymore.
- Now, you have a copy of your DVD video as an AVI file on your hard drive. You can play this using most media players. Unfortunately, as mentioned before, this file is usually too big to burn on a normal DVD disc.
Please note that if you have a video DVD that you cannot play in your ordinary DVD player because of region codes, either of the methods mentioned above will allow you see the DVD anyway, as the copies are not region coded. Of course, you can always watch the DVD on a region-free DVD player, or on your computer using a program like mPlayer.
Encryption and Signing
Cryptography can be used two ways: For digital signature and for secrecy. For both purposes, two digital number codes are used: One code that you keep hidden from everybody (called the private key), and one which can be published to everybody (called the public key). The two keys are constructed in such a way that if you use one of them for encryption, it is only possible to decrypt with the other key - and vice versa.
Secrecy
Secrecy (encryption) is done by using the recepients public key to lock (encrypt) the message. In this was it is only the recepient that can read the message - as he is the only one in posession of the private key that is needed to unlock (decrypt) the message.
Signing
A digital signature work just the opposite way. If the sender of a message locks (encrypts) the message with his private key, then it is only possible to unlock the message with his public key.
This implies that if a locked message only can be unlocked with the public key, then the message can only have been locked with the senders private key. And as the sender is the only one in possesion of the private key, he is the only possible sender.
Secrecy & Signing
Sometimes you wish both secrecy and signature, then you will combine the two techniques by first signing with the private key and then encrypting with the public key of the recepient. The recepient will now only be able to open the message with his private key and check the senders identity with senders public key.
Protection of data
If you just want to keep your own data a secret so that only yourself can read it, there is no need to have both a public and a private key. In this case, you only use one number code (called a symmetric key) that is constructed so that you can both encrypt and decrypt with the same key. This way you can protect your data, e.g. by encrypting your hard disk. As long as you keep the key to yourself, nobody else can access the data on the disk.
Practical uses
Most modern mail apprications already supports both encryption and signing using a standard called S/MIME. In order to use this, you only need to have a digital signatur/certificate. You can either buy one or make one yourself. In the latter case, you must be sure that whoever you communicate with, are informed about the socalled "fingerprint" of the certificate. Otherwise they will not know that it is you, they are communicating with.
Alternatively, you can use another standard, called GnuPG (GNU Privacy Guard). There is a lot of free software that supports it, but in most cases, you will have to install a plug-in in your mail reader to use it. The basic technology is the same in the two standards.
Political perspectives
As many other things secrecy and signing is a two edged sword: It can be used or abused.
In order for it to work, the most basic condition is that you must be absolutely sure that you alone know and have access to your private key. What could happen if somebody (i.e. an intruder) copied your private key and signed an instrument of debt with it? Will you then be in a better or worse position compared with a forged signature on paper?
Cryptography can also be used to prevent unauthorized persons getting access to private information. For example you can make sure that private documents can not be read by the thief who stole your laptop. But what happens if tax authoroties accuse you for cheating and beleive that the proof is on your computer? Can they demand for you to give them your private key? What happens if you do not deliver this private key?
The digital signature and cryptography can have several good uses and will be a part of the digital society of the future. But it is of utmost importance that everyone involved know how to handle it. We all have a lot of experience with hand-written signatures and door locks, and the juridical system have lots of precedence in court on these matters. The digital versions, however, work differently, and very little has shown up in court yet.
Therefore it is important that we are cautious and do it right. Both legally, technologically and educationally.
Disk encryption under Windows and Linux
TrueCrypt is able to encrypt disk partitions or whole disks and there is a version for both Windows as well as Linux
Under Linux you can use LUKS for the encryption of disk partitions. LUKS is even able to make a "Full Disk Encryption". That implies that the whole disk, except the Linux kernel and maybe some drivers, will be encrypted. In this way you are sure not to leave any tracks or confidential information in unencrypted files. If you do not want to encrypt all your data, Linux also offers "encfs" which allows you to encrypt single directories.
MACchanger
There are two addressed that identify your computer: the IP address and the MAC address.
The IP address is used on the internet when data is transmitted back and forth accross the planet. Typically you will get another IP address if you move your computer to another place.
The MAC address is only used on the local network - i.e. the network in the building where your computer is connected. The MAC-addres is coded into your network interface card by the factory and will never change, no matter where you connect your computer.
Usually, your computer automatically gets its IP address from a router or server when you connect your computer to the local network. This router or server will then remember which MAC-address (and thereby also computer) is connected to which IP-address.
This implies that if e.g. you are using an internet café, then you risk being traced. You get your IP address from the server on the interernet café. From the whole world, this IP-address can be traced back to the café. And the internet café will know that this IP address was used by a computer with your MAC address. If you later on return to the internet café, then can recognize you on the MAC-address. Apart from that, factories and resellers know the MAC address of the PC they sold you.
The bottom line is that you can be traced by your computer's MAC address. Luckily, it is possible to change the MAC address set by the factory.
The program MACchanger can do this for you automatically. It simply makes up a random MAC-address and tells your network card to use that instead of the one set by the factory. We have configured this CD in such a way that MACchanger automatically will do this everytime you boot your computer from the CD, before your network card is used.
Using MACchanger assures you that even if your IP address is traced back to the internet café, it will be difficult to determine exactly which one of the guests in the café used the IP address. If you turn off your computer, it will be impossible to know who had that random MAC address.
This can for example be used for making an anomynous phone call. Read more about this under IP Phone.
Political perspectives
Politicians often argue that more surveillance is needed in order to catch criminals like terrorists and pedophiles. Just as you can protect your privacy by using the tools on this CD, so can terrorists and pedophiles as well. Just like you can have a phone conversation from an internet café, a criminal can distribute child pornography without being tracked.
For this reason it will not help increasing surveillance; it is too easy to circumvent - in a completely legal way. Increased surveillance will only harm innocent private citizens.
Considerable public and private resources are wasted on useless surveillance that infringes on the citizens' privacy. These resources can be put to better use by allocating them to traditional investigation of criminal activities.
mPlayer
Playback all sorts of media
Often there are technical limitations on what you can do with DVD's, on-line videos etc.
Two examples:
- Some DVD-players will only play DVD-movies from a certain part of the world (because of so called region codes)
- Many software programs (including RealPlayer og Windows Media Player) will not let you make a personal copy of a media file.
Such limitations are typically introduced by the companies behind the media players in cooperation with the movie and recording industry. They are usually not based on legislation, and because of that you probably do not need to respect them. (Read more about this in k3b).
We have installed the media playser mPlayer with necessary codecs on this CD. With mPlayer you can watch all sorts of DVD's, on-line videos etc. without technical limitations.
Using the program mEncoder you will even be able to save what you have seen or heard in mPlayer. Unfortunately, the is yet no graphical interface for mEncoder, but if you open a terminal window, it is easy to download any video stream with this comand:
mencoder -o FILENAME -oac copy -ovc copy LINK
This will save the video stream LINK in the file FILENAME.
For Windows
mPlayer is also available for Windows, but VLC is better suppored by Windows. VLC is also included on this CD
For Mac and other platforms
Download VLC from the internet.
IP-phone
Use the phone over the internet
As you can read on the page about TOR, new so-called "laws against terror" have been introduced in several countries in the wake of September 11th, 2001. This legislation permits increased eavesdropping of telephone and data transmission. One result of this is that it has become a lot more easy for the police and the intelligence agencies to find out whom you are speaking to on your phone. In many countries, they do not even need a permission from court!
If you are not happy with this sort of surveillance, it is still possible to avoid it. One possibility is using phone over the internet.
Phone over internet comes in different versions. You might have heard of Skype, but we in IT-Political Association of Denmark recomend you to use SIP or another open standard. That way you have the possibility of choosing a provider that you like and trust.
Anonymity can be secured by registring a SIP accout with a provider that does not ask for any legitimation. If the provider does not know you, it is impossible for the police to force information about you from him. If you cannot find such a provider in your country, you can even use a foreign provider.
With your anomynous IP phone account you can walk into an internet café and use your laptop as a telephone - or take a SIP phone with you. Maybe you can just find an open wireless network. In this way it is impossible to figure out who you are when you call somebody.
If your friends also have an anomynous IP phone account, then you can have conversations that are impossible to track. You can also use an encrypted version of SIP so that is impossible to listen in on your conversation. And if you use the same provider, it is often free.
This demonstrates how futile many of the IT related anti-terror initiatives are: several ways to avoid eavesdropping and tracing exist - and they are all completely legal.
As a result the anti-terror laws only harms the innocent citizens, and the laws do not give the desired results.
Try it yourself
If you have a microphone and speaker/headphones attached to your PC, then you can try out internet telephony.
IT-Political Association of Denmark have made a SIP-registration with a Danish SIP provider, Musimi, and paid a small amount of money to that accout. As long as some money is left on this account, you can have a free call with this CD. Using a internet café or a wireless network, it will be impossible to trace you.
The only thing you have to do, is to open the program "Twinkle", on the desktop. In the field "Call" you type in the number, you want to call. Note: Since our SIP provider is located in Denmark, you have to enter 00 + the international code for your country before the number (e.g. 0032 for Belgium and 0049 for Germany). Clicking the "Dial"-button starts the call!
A lot of people probably want to try this, so keep your conversation short - there is a fixed amount on the account, and it will only work as long as there is any money. We have made a limitation so that it will only work with phone numbers that are reasonably cheap to call from Denmark.
You should also be aware that everyone trying this CD will use the same phone number. They cannot listen to your conversation, but if someone tries to return your call, the IP-phone will ring at everyone using this CD at the same time.
Further anonymity
If you use a IP-phone on an internet café or using a open wireless network, the only thing that can be tracked is that the phone conversation was done by somebody on said internet café/network. If the police gets access to this network, they might recognice your so called MAC address. To avoid this, you can use MACchanger, which also is installed on this CD.
If you also want to avoid the risk of being traced to the internet café or network you are using, you can use TOR to anonymise your internet traffic. However, this delays the traffic a bit, so it is best used for mail or file exchange. At this point, we cannot recommend TOR for phone calls.
For Windows and MAC
ZPhone is not Open Source and for that reason, it is not included on this CD. But ZPhone is free of cost and available for Windows, Mac OSX and Linux.
...and other interesting platforms
miniSIP is an open source SIP client with encryption. It runs on Windows XP, Pocket PC, and Nokia Internet Tablets (Maemo). Use a PDA with WiFi and you have a cheap or free end-to-end encrypted alternative to mobile phones. Coverage is not as good as with normal mobile phones (e.g. GSM), but it is cheap and will not be tracked, eavesdropped or registred.
OpenMoko is an attempt to make a mobile phone completely based on open source software. It runs linux and has both GSM and WiFi, so it will probably be able to run an open source encrypted SIP client (like Twinkle). At the time of writing (February 2008), the final version of the first OpenMoko phone is not released, but check the web site for details.
TOR
The Onion Router
After 9.11 2001 there has been much interest for fight against terror. Because of that, many countries have introduced new restrictive anti-terror laws supposed to stop terrorism.
A common measure is to log and spy on everybody and everything they do on the internet. This has eliminated much privacy, but it has not stopped terrorism. Fortunately, there are tools to protect the privacy of law-abiding citizens.
Let us introduce one of these tools- TOR - The Onion Router. TOR was originally developed by US Navy to protect the identity of its agents. It can be used by everybody that do not want to be surveilled. The tools are fully legal and impossible to track.
TOR works by sending the internet traffic from you on a detour through a network of servers, so it is no longer possible to see who you are communicating with. It works in the following manner:
In the diagram below, Alice wants to communicate with Bob without being tracked. Normally, she would just contact Bob through a direct connection, but with TOR she sends her messages to a random TOR-server - in the diagram TOR-server 1
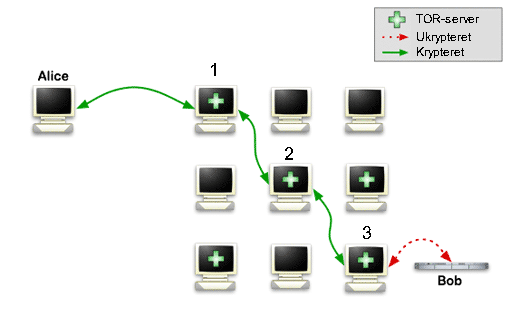
TOR-server 1 sends the message on to TOR-server 2 that sends it on to TOR-server 3 - which delivers the message to Bob. The trick is that TOR-server 1 only knows Alice and TOR-server 2 - but not bob and TOR-server 3. TOR-server 3 doesn't know anything about Alice.
In that way, Bob is not able to know where Alice is. And if you tap Alice's connection, then you can only see that she is talking to TOR-server 1. So you can't see that she is really talking with Bob. All the green connections in the diagram are encrypted, so it's not even possible to see what she is sending to Bob.
Even if the police or another agency seizes one or several of the servers they will not be able to see who is talking to who. To reveal this, they would have to control allthe TOR-servers in the world.
The only drawback about TOR is that the encryption takes time and therefore the connection, that Alice and Bobs communicate on, is not as fast as if they talked directly. But that is a small price to pay if you care about your privacy.
Try Tor for yourself
We have installled TOR on this CD. When you use the Firefox browser, your traffic will automatically be sent through TOR. If you use it to do email on e.g. Google mail, it won't be possible to see who you are mailing with by tapping your connection.
You can test TOR by visiting http://whatismyip.com/. This page will tell you which IP address you are using. The IP address is the adress that identifies your computer on the internet, which can be used to track you. If you visit the site several times, you will see that it thinks you are comming from different places all over the world.
For more reading about TOR, please visit tor.eff.org.
If you are reading this on a windows computer
You can run TOR on Windows by running xeroBank browser xB can be run without having to be installed on your Windows computer and without changing your registry database. xB first has to be unpacked on your harddisk or even better your USB media.
Actually it is a good idea to have xB browser on your USB key even if you normally don't use windows, because often you aren't near your own computer and you want to protect your privacy. Using xB from your USB media will definitly help you protect your privacy on a windows computer.
Wiping you hard drive
When you dispose of your computer, it is time to protect your privacy or trade secrets. After having copied all important files to your new computer, you have to remove all data on the old harddisk for good.
Simply deleting the files the normal way is not enough, as a normal delete does not really delete the files. It only only marks the files as deleted by removing them from the list of files. Until the files are physically overwritten on the hard disc, it is often possible to "undelete" them.
Wipe is a program that erases a file or a disk partition by overwriting it 34 times with different bitpatterns. It is a command-line program and in order to use it, you have to know how files and partitions are named in Linux. But it is probably a good thing that there is not just a menu option that erases your harddisk forever.
Wipe is invoked by typing the following in a terminal:
wipe filename
E.g. "wipe /dev/hda" vill erase the first IDE disk.
In Windows
For windows we recommend Eraser
Recycle harddisks
Many older computer are donated to charities like projects in the third world. Due to fear of leak of private information, more and more donaters physically destroy the harddisks before donating. But with a program as "wipe" it is possible to remove all data on the disk without destroying it. And by using Polippix you can do the wiping of the disk yourself.
Kommentar: RE: Polippix English Text
Hi there,
My name is Daniel. I saw that you mentioned a few IP tools here https://www.aktion-freiheitstattangst.org/de/articles/948-polippix-english-text.htm.
I tried.. but the tools are really messy and filled with so many ads - it was really hard to figure out what my real IP address was!
When I searched for alternatives, I came across this great tool: https://www.wizcase.com/tools/whats-my-ip/
It's very clear without any ads or promotional stuff. Most importantly, the data is accurate and easy to read. I think you'll find it useful for you and your readers. Will you consider adding this tool to your site as an additional resource?
Thanks
Daniel, 23.12.20 20:06
Category[40]: Anti-Überwachung Short-Link to this page: a-fsa.de/e/1gB
Link to this page: https://www.aktion-freiheitstattangst.org/de/articles/948-polippix-english-text.htm
Link with Tor: http://a6pdp5vmmw4zm5tifrc3qo2pyz7mvnk4zzimpesnckvzinubzmioddad.onion/de/articles/948-polippix-english-text.htm
Tags: #Polippix #CD #Umgehung #Ueberwachung #Datenschutz #Programme #LiveCD
Created: 2010-01-04 13:36:59
Kommentar abgeben




